Local area network LAN project of the Office building in Moscow
We completed the development of project documentation for the LAN of the local area network of the Office building in Moscow.
LAN DESIGN
Terms and Definitions
|
1000 Base-SX / LX / ZX |
Fiber optic connectivity interfaces defined in the Gigabit Ethernet standard (IEEE802.3z) |
|
1000 Base-T |
Copper cable connection interfaces defined in the Gigabit Ethernet standard (IEEE802.3ab) |
|
10GBase-SR / LR / ZR |
Fiber cable connectivity interfaces defined in 10Gigabit Ethernet IEEE802.3ae |
|
Unified Information System |
The set of software and hardware, information and organizational tools that provide input, transmission, processing and storage of information within the organization |
|
End user |
User using the services and services provided by LAN |
|
Local computing network |
The set of software and hardware tools providing information transfer within the building / group of buildings. |
General provisions
This project documentation on the local area network (LAN) in the building of the Administrative and business complex
Architectural and construction drawings and layouts of furniture arrangement;
Regulatory and technical documents.
Purpose of the LAN system
The main purpose of the Local Area Network (LAN) is to provide network interaction (data receiving / transmitting over a structured cable network and a wireless medium between LAN nodes (user workstations, equipping IT infrastructure systems) with active network equipment (ASO).
The LAN of the Customer’s building is intended for:
The exchange of information (including wireless) within a LAN between input devices, processing and storage of information through network interaction;
Ensuring the integration of the projected LAN into a single information system of the Customer;
Connecting the LAN of the building to the Customer's CSDD channels, and to the global network channels for various purposes;
Providing data transfer services within the office premises to related services and systems;
Providing access to wireless network services.
Objectives of the system
The main objectives of creating a LAN in the building of the Customer are:
Creating a network infrastructure that provides services to users;
Ensuring the possibility of effective access to common network information resources (database servers, corporate e-mail, etc.);
Ensuring the possibility of creating a unified information system uniting the Customer’s facilities;
Providing access to information systems for mobile users.
The list of regulatory and technical documents used in the development
When developing project documentation for this project, the following regulatory documents are used:
RF Decree No. 87 of February 16, 2008 “On the Composition of the Sections of the Project Documentation and Requirements for Their Maintenance”;
GOST R 21.1101-2013 Basic requirements for design and working documentation;
RFC 1918 The document addresses address allocation issues in private IP networks.
Characteristics of the automation object
For the system being created, the automation object (hereinafter the Object) is the building
The object is an 8-storey office building.
The number of cross rooms on the floors from the 2nd to the 8th is two for each floor, on the ground floor there is one cross-room.
Server room SK-1 is located on the 2nd floor of the building.
Between the cross-rooms, to create a structured cable network used by the LAN, it is possible to install a vertical cable system and connect it to the Horizontal cable systems of the floors.
Basic technical solutions
Basic Design Principles
The basis of building a LAN is based on the following principles:
Security - equipment used to build a LAN supports security mechanisms and protection against unauthorized access.
Versatility - equipment used to build a LAN, supports open protocols and standards, and supports collaboration with equipment from various manufacturers.
Scalability - LAN provides an opportunity to increase the system capacity by the number of simultaneously working users or by supporting new technological solutions and protocols without additional work related to intervention in the capital elements of the building structure, cabling and installing additional connectors.
Reliability - in case of failures, the system provides a mechanism to restore the availability of resources by automatically switching to the backup node.
Durability is a quality guarantee for the system components issued by the manufacturer of the system equipment and for the work performed by the Contractor; the possibility of providing technical support for LAN components by the system equipment manufacturer after the expiration of the warranty.
Ergonomics - solutions used to build a LAN, provide for easy repair and restoration of the system, ease of maintenance and network administration with minimal operating costs.
Aesthetics - LAN meets modern aesthetic requirements.
Cost Effective - LAN supports reduced operating costs.
Unification and Standardization - LAN provides equipment manufactured by Cisco Systems. The equipment has a single operating system for all IOS devices (Internetworking Operating System). When designing, a unified model range was used, which allows for interchangeability of the chassis, power supplies, modules and reduce the cost of spare parts. All equipment has certificates of SSE (Electrosvyaz Certification System) and the Ministry of Communications of Russia.
Multiservice - the system provides the ability to simultaneously transmit data, voice and video based on the technology of quality of service (QoS) for various types of traffic, taking into account their priority.
General provisions
The choice of technology, architecture and active network equipment for a LAN is determined by the following factors:
Network size and number of users;
The need to ensure user access to all permitted network and information resources;
The need to divide users into work groups using virtual networks;
Providing guaranteed high-speed connections for servers and workstations, regardless of the workload of individual segments and network equipment;
The possibility of increasing the number of workstations and servers and expanding the network without disrupting its operation;
Minimization of the range of equipment used to reduce administrative costs;
Supporting the quality of service;
Service level management;
Compliance with international standards.
LAN provides data exchange with the following bandwidth:
between devices of the access level subsystem and devices of end users - at least 1 Gbit / s;
between the devices of the access level and the kernel level subsystems - at least 10 Gbit / s for each communication channel;
between the LAN core and the SK-1 server farm core - at least 10 Gbit / s for each communication channel;
between devices of the server farm level subsystem and server equipment - at least 10 Gbit / s for each communication channel for blade servers and at least 1 Gbit / s for each communication channel for rack-mounted servers;
between devices of external communication subsystem and LAN core subsystem - at least 1 Gbit / s for each communication channel.
The basic network protocol supporting transport on a LAN is IP. The third and fourth layers of the OSI model are TCP / IP version 4 protocols. The IP addressing plan of the LAN complies with RFC 1918 and takes into account existing IP addressing plans in adjacent external systems, as well as a 30% increase in the number of network devices.
The naming of active network LAN equipment takes into account the existing corporate equipment naming policy.
Solutions on system structure and means of communication between components
The chosen solution for the construction of a LAN is based on the requirements for the construction of local computer networks with a clear delimitation of hierarchy levels, where each hierarchy level has its own set of equipment that performs certain functions for this level. When building a LAN, the classical model is used, according to which there are several levels of the network hierarchy: the core level, the distribution level, and the access level. At the same time, the core level and the distribution level are combined into a single core level.
LAN includes the following subsystems:
Access level subsystem - provides connection of end-user devices, WLAN access points, ITS subscriber devices, MMS, video conferencing terminals and other network equipment of adjacent systems;
The kernel-level subsystem combined with the distribution level provides high-speed switching between components: user devices, information processing and storage devices;
Server farm subsystem - provides functions for connecting local LAN servers and server equipment of adjacent systems: ITS, MMS, etc.
WLAN subsystem - a subsystem that provides the ability to exchange data using wireless technologies (Wi-Fi);
External Connections Subsystem - a LAN subsystem that provides connection to external communication channels (Customer's SPD channels, Internet channels);
Management and Monitoring Subsystem - provides centralized management and monitoring of the state of network equipment.
The hierarchical model of LAN construction allows to provide fault tolerance, multiservice, the possibility of further expansion of the LAN without reducing performance indicators.
A diagram of the connection of functional components of a LAN is shown on sheet 2, “Functional Diagram,” of the documentation set for the SEIV.24872-LAN.
A diagram of the connection of LAN elements is given on sheet 3, “The Structural Diagram,” of the documentation set for the SEIV.24872-LAN.
Solutions for a set of technical tools
LAN Core Subsystem
The subsystem consists of two modular level 3 switches (L3) based on the Cisco Nexus 7706 chassis and a N77-SUP2E control module (with the Cisco NX-OS operating system and licenses that support routing between LAN segments). Each kernel switch contains two control modules. The core level switches are located in the HCC room.
The termination of fiber-optic trunk lines of 10 Gbit / s from access switches, from the switches of the SK-1 server farm core, is carried out on the N77-F348XP-23 boards (provided for 2 boards per chassis). Each of the boards contains 48 ports with an SFP connector for installing 1 GBase / 10 GBase transceivers (1/10 Gbps).
Between themselves, the core switches are connected via 2 optical communication channels with a bandwidth of 10 Gb / s, the termination of which occurs on the N77-F348XP-23 interface modules.
Communication channels from connected switches are combined into Multichassis EtherChannel (Virtual Port Channel technology, vPC), forming a coherent channel and providing fault tolerance of the solution when one of the core switches fails. A diagram of the formation of virtual communication channels on the core switches is shown in Fig. 2
To work with vPC, additional connecting links between core level switches are also required (Fig. 2):
1) vPC peer-link to synchronize configurations;
2) vPC keepalive to monitor the state of the neighboring device.
The vPC peer-link channel is formed using 2 optical communication channels with an aggregate bandwidth of 20 Gbit / s (2 × 10 Gbit / s), the termination of which occurs on different N77-F348XP-23 boards using SFP-10G-SR transceivers.
The vPC Keepalive channel is formed on the basis of 2 copper communication channels with a bandwidth of 2 Gbit / s (2x1 Gbit / s) terminated on N77-F348XP-23 boards using GLC-T transceivers.
The core switches have 2 power units of 3000W each, in a fail-safe redundancy mode.
LAN access level subsystem
The access level subsystem of the main LAN is based on Cisco Catalyst 3850 Series OSI Layer 3 Layer Switches, model WS-C3850-48F-E.
Depending on the density of ports in the floor cross-room premises, there are from 2 to 4 switches connected in a stack with a single control and switching center.
Each stack of access switches is connected to the core switches by 10 Gbps fiber-optic communication channels terminated on different switches from the core and on different switches of the access stack.
Logically trunk connections are combined into a single channel using Etherchannel technology (Multi-Chassis Etherchannel (MEC) from the core). Such a combination allows increasing the throughput of inter-level communication channels and provides fault tolerance of the solution in case of failure of a single communication channel or a switch terminating this channel.
To connect end devices, each switch contains 48 ports with a 1000Base-T standard RJ-45 connector with PoE + support (IEEE 802.3at standard). The total PoE power is 800 watts in total per switch.
The connection of user workstations is realized through one network interface (the connection of the user's workstation is carried out through a telephone set). Access switches support Power over Ethernet Plus technology on all copper interfaces, providing power to ITS IP phones over a structured cable network. CDP is used to detect the connection of the telephone to the switch port. During the exchange, the switch instructs the IP phone to forward packets related to voice traffic in a tagged form using a voice VLAN. At the same time, traffic from the workstation is transmitted in untagged form.
Access switch ports provide initial isolation of the traffic of various information systems on different VLANs.
Server farm subsystem LAN
The server farm subsystem is implemented in the room SC-1.
The server farm subsystem SK-1, located in the room SK-1, is a data processing center (hereinafter referred to as the data center).
The data center includes the following modules:
Datacenter Core Module;
Data center distribution module;
Data Center Access Module.
The data center core module is implemented on the basis of two modular Layer 3 switches (L3) based on the Cisco Nexus 7706 chassis and the N77-SUP2E control module (with the Cisco NX-OS operating system and licenses that support routing between LAN segments). Each core data center switch contains two processor modules.
The termination of 40 Gbit / s fiber-optic trunk lines from distribution switches of the server farm is carried out on the N77-F324FQ-25 boards (there are 2 boards for each chassis). Each of the boards contains 24 ports with a QSFP connector for installing 40GBASE (40 Gb / s) transceivers.
Connections between data center kernel module switches:
The vPC peer-link channel is formed using 2 optical communication channels with an aggregate bandwidth of 80 Gbit / s (2 × 40 Gbit / s), the termination of which occurs on different N77-F324FQ-25 boards using QSFP-40G-SR-BD transceivers .
The vPC Keepalive channel is formed on the basis of 2 copper communication channels with a bandwidth of 2 Gbit / s (2x1 Gbit / s) terminated on N77-F348XP-23 boards using GLC-T transceivers.
The data center core switches each have 3,000 W power supply units, in fail-safe redundancy mode
The data center distribution module is implemented using 4 Cisco Nexus 5672UP switches, each of which contains 32 slots for installing SFP / SFP + / FET transceivers and 16 Unified Ports slots for installing transceivers of different types (SFP / SFP +, FET, Fiber Channel). Blade chassis are connected to these switches via 10 Gb / s optical communication channels.
Each Cisco Nexus 5672UP switch contains 6 QSFP 40GBASE ports for trunk connections:
4 ports for connecting to Cisco Nexus 7706 data center core switches;
2 ports for organizing vPC peer-link connections between Nexus 5672UP pairs.
Connections between pairs of Cisco Nexus 5672UP switches:
The vPC peer-link channel is formed using 2 optical communication channels with an aggregate bandwidth of 80 Gbit / s (2 × 40 Gbit / s) using QSFP-40G-SR-BD transceivers.
The vPC Keepalive channel is formed on the basis of 2 copper communication channels with a bandwidth of 2 Gbit / s (2x1 Gbit / s) terminated using GLC-T transceivers.
LAN DESIGN DOCUMENTATION
Upstream connections of server farm switches installed in different rack rows are combined in pairs into a fault-tolerant logical channel using vPC, as shown in Figure 5.
The data center access module is built on expansion switches: Cisco Nexus C2348TQ, Cisco Nexus C2348UPQ.
Customer servers connected to SK-1 racks are connected to these switches.
Each Cisco Nexus C2348TQ switch is equipped with 48 100M / 1 / 10GE ports with RJ-45 connectors for connecting server hardware.
Each Cisco Nexus 2348UPQ switch is equipped with 48 SFP / SFP + slots for installing copper or optical transceivers for connecting server hardware.
Cisco Nexus 2300 expansion switches connect to Cisco Nexus 5762 data center distribution switches using FET-10G (Fabric extender transceivers) interfaces.
Subsystem external connections
The subsystem of external connections provides connection to external communication channels (including the Internet), excluding channel-forming equipment.
The external interaction subsystem consists of:
Two Cisco ASR1002-X routers that terminate external communication channels from two different providers of access to the global Internet.
Two Cisco ASR1002-X routers, which terminate the external communication channels of the corporate SMS network.
Two Cisco ASA 5545 firewalls in a fault-tolerant configuration to ensure a secure connection to external communication networks.
Two switches Cisco Catalyst 3850, to ensure connectivity to equipment providers.
Devices are complemented by redundant power supplies for fault tolerance.
Firewalls will provide access control between external networks and LANs, protecting the internal network infrastructure of the Customer from external threats;
Firewalls will have the following functionality:
Fault tolerance (Active-passive failover);
Filtering in the routing mode (routed);
Security Policies (Access Control Lists), which will be determined at the implementation stage by requests from adjacent systems and data from the Customer.
Cisco Catalyst 3850 switches (24 RJ-45 Gbase-T ports) switch traffic between external connections, firewalls, and the network core.
Management and Monitoring Subsystem
To remotely control and monitor the status of network devices in a LAN system, the project involves the use of the Cisco Prime Infrastructure software and hardware. The Cisco UCS C240 M3L server and the VMware vSphere 5 system platform are used as the hardware platform.
The infrastructure of Cisco Prime Infrastructure includes:
Cisco Prime Network Control System (NCS) - provides converged user and access management, complete wireless network lifecycle management, and integrated configuration and control of routers in branch offices;
Cisco Prime LAN Management Solution (LMS) - simplifies the management of networks without boundaries of Cisco and reduces operating costs, adjusting the functions of network management to the methods of network operators.
The Cisco Prime Infrastructure Management System provides the following features:
Centralized management of LAN network devices:
Configuration, change and compliance management;
Archive of device configuration files;
Collection of inventory information.
Monitoring network LAN devices:
Collection of critical (level critical) syslog messages;
Monitoring versions of images of installed operating systems.
Graphical interface for monitoring switches and LAN routers;
Access to the Cisco Knowledge Base;
Monitoring LAN performance and applications;
Identification of unauthorized access points and client devices on the map.
The WLAN subsystem provides connection of end-user devices, devices of adjacent systems through a wireless data transmission medium Wi-Fi.
The WLAN subsystem consists of:
Base stations (access points) that directly service and connect end-user subscriber devices. Available in Cisco Aironet 3700 Series Dual Band Access Points.
WLAN controllers that provide centralized control of WLAN base stations. The project uses Cisco AIR-CT5508 controllers.
The wireless access level module is implemented as Cisco AIR-CAP3702 base stations (access points);
The wireless subsystem includes 200 access points AIR-CAP3702.
Cisco Aironet 3702 access points support IEEE 802.11a / b / g / n / ac wireless standards and have an integrated spectrum analyzer (Cisco CleanAir technology). As antennas, dipole omnidirectional antennas of the 2.4 and 5 GHz bands are used, built into the monoblock, intended for installation on a suspended ceiling, or behind it.
Access points are connected to a LAN via 1000 Base-T channels via LAN access level switches. The access points are powered by these switches using power technology via unshielded IEEE 802.3at (PoE +) unshielded twisted-pair cable.
The selected points belong to the Lightweight series, which means that only centralized control is supported using a wireless access controller. This approach provides increased security and convenience of control points, a great potential for the development of the system.
The planned placement of access points is shown on the “Equipment Location Plan” Sheet 3 of the sets of documents YuIVE.24872-LAN.
The main functions of access points:
Connecting client devices according to IEEE 802.11a / b / g / n / ac wireless standards;
Encryption of user traffic in the wireless channel;
CAPWAP-tunneled user traffic in the wired segment.
Distribution of access points
The number and location of access points is selected based on the following factors:
Requirements of TZ and wishes of the Customer regarding the coverage area: all office premises (including elevator halls, transitions and stairs);
The requirements of TK regarding the need to locate WLAN clients;
Recommendations of the manufacturer of equipment Cisco Systems regarding the construction of a wireless network with the presence of a positioning service.
The requirements of TK regarding the use of WLANs for the operation of Wi-Fi telephony.
The number of access points should be specified at the commissioning stage. If, as a result of radio surveys, the number of installed access points decreases, they should be used as a zip.
The estimated number of access points used to cover the required zones is 200 points.
As a result of the radio modeling, layouts were developed indicating the locations of access points.
The main purpose of the wireless access controller is centralized control of the access points used in the project and dynamic radio frequency control. The controller initiates a secure connection with points via the CAPWAP protocol (Control and provisioning of wireless access points), and performs their programming on certain settings, which eliminates the possibility of unauthorized configuration changes.
At the initial wireless infrastructure initialization stage, non-overlapping channels are automatically assigned to access points. Analyzing the signal strength in the channels, the controllers are able to make a decision to build the optimal radio frequency network topology in a dynamic mode, which will make it possible to expand the boundaries of the wireless network without significant time and cost: the new points will get the optimal settings automatically and do not require reconfiguration of the old components.
For WLANs, it is suggested to use the Cisco Wireless Controller 5760 Series Controllers (AIR-CT5508-250-K9). The controller supports up to 250 access points, which provides guaranteed service to all points and contains stock to expand the system in the future.
Basic functions of WLAN controllers:
Ensuring secure seamless roaming (L2 and L3);
Automated control of radio (frequency and power of access point transmitters);
Elimination of "holes" in the coating in case of failure of access points;
Switching users from loaded points to less loaded ones;
Detection and elimination of interference (mutual negative influence) between their access points and with outsiders;
Detection and elimination of the negative impact of interference on the operation of a WLAN;
Wireless Intrusion Detection;
Ensuring security policies;
Providing Wi-Fi Multimedia Policies (WMM) (Wireless QoS);
Providing guest access service (web-authentication).
WLAN Physical Topology Solutions
Informational interaction between WLAN components is carried out via LAN.
Access points are mounted on the installation site, located behind the suspended ceiling, according to the scheme of placement of access points. An unshielded twisted pair not lower than category 5e is supplied to the location of each access point. Wireless access points are connected to the floor switches of the LAN access level via twisted pair using 1000BASE-T technology.
WLAN controllers that control the access points are located in the main cross-room and are connected to the LAN core switches.
Equipment Naming Solutions
Naming of network equipment should be implemented as follows:
Code - Platform - Membership - Placement Code – Order Number
Decryption:
Code — equipment type identifier (SW — switch, R — router, FW — firewall, AP — access point, WLC — WLAN controller).
Platform - indicates the platform / model / equipment series:
N7k - Cisco Nexus 7706;
N5k - Cisco Nexus 5672UP;
N2k - Cisco Nexus 2300;
3850 - Cisco Catalyst 3850;
1002 - Cisco ASR1002-X;
5545 - Cisco ASA5545;
5508 - AIR-CT5508.
Functionality - the identifier of the functional belonging:
core - subsystem of the LAN core,
cod - server farm subsystem
acc - LAN access subsystem,
wan - subsystem of external connections of LAN,
wlan - subsystem WLAN.
The Location Code - the room code (cross), where the device is installed, is not indicated if the device is logical, the physical parts of which are located in different rooms. The code can take the values FC- [01-08] [A / B] (cross-rooms, floors). The main cross room is designated MC.
OrderNumber - serial number of the device (only if there are several devices of the same type)
Solutions for the placement of a set of technical equipment on the object
LAN access level equipment should be located in the switching rooms of the building’s floors, referred to in the SCS project terminology - cross-rooms of the floor (KKE). The equipment of the core level, the subsystem of external interactions is located in the main cross room (GKK).
Equipment server farm LAN is located in the server room SK-1.
The location of the equipment in the cabinets is presented on sheets 5.1-5.17 of the design documentation for the JEWE.24872-LAN (ECPR15.001-LAN).
LAN logical topology solutions
At the second level, the LAN is logically differentiated into segments based on the technology of virtual VLANs. Virtual networks allow you to control the size of broadcast domains, as well as regulate access between them using access lists. For the structure connectivity, all the inter-switch ports (including the aggregated EtherChannel and vPC) are configured in Trunk mode with the resolution of all VLAN traffic.
Ports of client equipment are configured in Access mode with a binding to the corresponding VLAN.
Logical topology level 2 solutions
To ensure reliability and fault tolerance of the LAN, as well as to increase the capacity of communication channels, the project provides for the aggregation of inter-switch communication channels.
Each access switch is connected to the core level switches with at least two independent optical communication channels with a bandwidth of 10 Gb / s each. The termination of communication channels on the core switches is carried out on different interface modules, which are installed two per each core switch. Two communication channels between the core and access switches are combined into one logical channel (Multi-Chassis EtherChannel for access switches, vPC for core switches and a local server farm) using the LACP aggregation protocol.
Ports that form such channels have a common identifier of the aggregated channel and are configured on both sides in active mode. All link layer settings (encapsulation, VLAN, trunk, etc.) are applied on this logical port.
In order to achieve optimal loading of each of the physical channels included in the EtherChannel, load balancing is performed. The balancing parameters are the IP addresses of the source and destination of the packet. They are processed using a special mathematical function, the result of which is the physical port number in the EtherChannel through which the frame must be sent. This type of balancing allows you to achieve a stable path for all packets between each pair of interacting devices.
SW-N7K-core-mc-1
Create a VPC domain with the identifier "1"
Create a peer-keepalive channel to monitor the state of a neighboring device using keepalive messages:
Physical interfaces: 1/46, 6/46
interface: port-channel 200
vrf: management
ip address destination: 10.178.255.14 / 30
ip address source: 10.178.255.13 / 30
Create a peer-link channel for configuration synchronization:
Physical interfaces: 1/45, 6/45
interface: port-channel 201
switchport mode trunk
switchport trunk allowed vlan
vpc peer-link
Create vPC channels to downstream devices:
switchport mode trunk
other settings according to table 2
SW-N7K-core-mc-2
Configuring the SW-N7K-core-mc-1 is similar to SW-N7K-core-mc-2, except for the following settings:
peer-keepalive channel:
ip address destination: 10.178.255.13 / 30
ip address source: 10.178.255.14 / 30
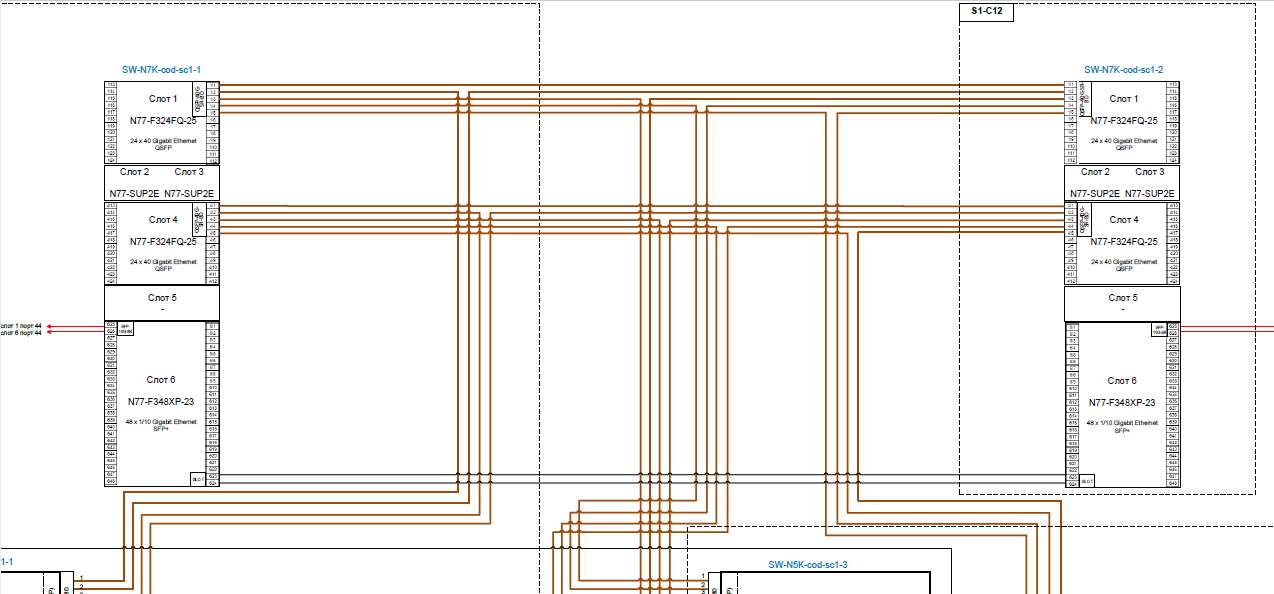
SW-N7K-cod-sc1-1
Create a VPC domain with the identifier "1"
Create a peer-keepalive channel to monitor the state of a neighboring device using keepalive messages:
Physical interfaces: 6/23, 6/24
interface: port-channel 200
vrf: management
ip address destination: 10.178.255.2 / 30
ip address source: 10.178.255.1 / 30
Create a peer-link channel for configuration synchronization:
Physical interfaces: 1/1, 4/1
interface: port-channel 201
switchport mode trunk
switchport trunk allowed vlan
vpc peer-link
Create vPC channels to downstream devices:
switchport mode trunk
other settings according to table 18
Tab. 18.
SW-N7K-cod-sc1-2
Configuring the SW-N7K-core-sc1-2 is done in the same way as the SW-N7K-core-sc1-1, except for the following settings:
peer-keepalive channel:
ip address destination: 10.178.255.1 / 30
ip address source: 10.178.255.2 / 30
SW-N5K-cod-sc1-1
Create a VPC domain with the identifier "2"
Create a peer-keepalive channel:
Physical interfaces: 0/31, 0/32
interface: port-channel 200
ip address destination: 10.178.255.5 / 30
ip address source: 10.178.255.6 / 30
Create a peer-link channel:
Physical interfaces: 1/5, 1/6
interface: port-channel 201
switchport mode trunk
switchport trunk allowed vlan
vpc peer-link
Create vPC feeds to upstream devices:
switchport mode trunk
other settings as per table 19
SW-N5K-cod-sc1-2
Create a VPC domain with the identifier "3"
Create a peer-keepalive channel:
Physical interfaces: 0/31, 0/32
interface: port-channel 200
ip address destination: 10.178.255.9 / 30
ip address source: 10.178.255.10 / 30
Create a peer-link channel:
Physical interfaces: 1/5, 1/6
interface: port-channel 201
switchport mode trunk
switchport trunk allowed vlan
vpc peer-link
Create vPC feeds to upstream devices:
switchport mode trunk
other settings according to table 20
SW-N5K-cod-sc1-3
Configuring SW-N5K-cod-sc1-3 is done in the same way as SW-N5K-cod-sc1-1, with the exception of the following peer-keepalive channel settings:
ip address destination: 10.178.255.6 / 30
ip address source: 10.178.255.5 / 30
SW-N5K-cod-sc1-4
Configuring SW-N5K-cod-sc1-4 is done in the same way as SW-N5K-cod-sc1-2, except for the following peer-keepalive channel settings:
ip address destination: 10.178.255.10 / 30
ip address source: 10.178.255.9 / 30
Virtual VLAN Organization
An integral component of the solution is the technology of delimiting network segments using virtual VLANs.
Virtual networks allow you to control the size of broadcast domains, as well as regulate access between them using access lists. On each access switch, clients of different information systems are isolated by different VLANs.
The functional purpose of the VLAN in the framework of the system:
selection of device control segments in a separate subnet;
segment delimitation in order to isolate network flows.
The composition of VLANs is given in Table №№ in section 3.8.
WLAN Logical Topology Solutions
Customer access switch ports, to which access points are connected, are placed in access point virtual networks. These subnets are intended for addressing the management interfaces of access points. In addition to the IP address, subnet mask and IP address of the gateway, the DHCP option 43 provides access points with the IP addresses of the management interfaces of the wireless network controllers. Using this information, the access points initiate the process of connecting to the controller via the CAPWAP protocol, during which two encrypted tunnels are built, one for control and the other for transmitting data from wireless clients. After successful registration of the points on the controller, the controller updates the software of the access points and settings files of the access points, if necessary.
Connect wireless devices to the desired WLAN by SSID. Depending on the selected SSID, security and access control policies are applied to the wireless client corresponding to this group. After successful authentication and authorization, users of each group are placed in a virtual network (VLAN) for their group.
Routing between the virtual WLAN subnets and other networks is performed on the LAN core switch, for this the corresponding Interface VLANs are created on the core switch. The kernel's Switch Interface VLAN IP Addresses act as default gateways for their subnets. In order to isolate traffic between different WLAN segments, access lists are configured on the kernel switch interface VLAN.
On the controller, the SSID is bound to a specific VLAN. Addresses for connected devices must be assigned using the Customer’s existing DHCP server.
For each information system, a range of non-public IP addresses is allocated in accordance with RFC 1918 from the range of IP addresses allocated by the Customer
Kernel switches are a central element in the Layer 3 logical topology, providing traffic routing between different LAN segments. For routable VLANs on the kernel switches, virtual interfaces are configured, which are the routing points for the corresponding VLANs.
There is a default gateway reservation for end devices and a server farm using HSRP. In order for HSRP to work in each VLAN, the first three IP addresses of the subnet must be reserved.
Tab. 22. Addressing management interfaces
LAN Reliability Solutions
The basis of building a LAN is the principle of reservation of the main elements:
Redundant kernel level switches;
Redundancy of interface modules in each core switch;
Backup routers connect to external networks;
Redundant power supply of network devices;
Reservation of communication channels between network devices and their termination on various LAN devices.
Thus, the use of multi-level redundancy allows you to avoid idle LAN in case of failure of one device, its module or the interruption of the communication channel.
Decisions on the number and qualifications of staff
The network administrator must have a high level of qualification and practical work experience sufficient to carry out configuration, administration, and troubleshooting operations of software and hardware used in the system.
The network administrator of the LAN should monitor the state of the system elements, directly participate in the diagnosis and repair of equipment in case of emergency situations, carry out preventive maintenance work and take part in the modernization of the system.
The main duties of a network LAN administrator include:
upgrading, tuning and monitoring the performance of a set of technical means (active network equipment and LAN management servers);
update, configure and monitor the health of the system software.
To maintain the system, you must have at least two employees in the “Network Administrator” position with qualifications at the level of CCNP: Cisco Network Technologies Professional. To achieve this qualification, the following training courses are needed.
ROUTE course (exam 642-902). Implementing routing in Cisco networks.
SWITCH course (exam 642-813). Implementing Cisco Switched Local Area Networks
TSHOOT course (exam 642-832). Troubleshooting, maintenance of Cisco IP networks.
642-637 SECURE (Securing Networks with Cisco Routers and Switches - Securing Networks with Cisco Routers and Switches).
The employee can combine the maintenance of this system with other systems with an appropriate level of qualification.
Solutions to protect information from unauthorized access
Routers and LAN switches support the following information security technologies:
Filtering processed traffic based on defined rules
Restricting access to control and monitoring mechanisms
Authentication of network administrators,
Access Control (Network Access Control),
RADIUS or TACACS + protocol support,
Support for protection against unauthorized access to system audit protocols,
Support for connecting LAN administrators to control via SSH.
The system equipment is located in places with limited access.
LAN Interconnection Solutions with Adjacent Systems
List of systems with which LAN is connected
LAN is interconnected with the following systems:
Structured Cabling System (SCS)
Power supply system;
Ventilation and air conditioning system;
Structured Cabling System (SCS)
SCS should provide the ability to connect switches, according to the required structure of the network, shown in the block diagram of the LAN.
SCS should provide connection of base stations within the building in accordance with the equipment layout plan.
A cable reserve must be provided in order to change the location of the access point in a radius of 5 meters.
It is necessary to reserve a place in the cabinets of the floor cross rooms and in the server room for the installation of the equipment of the system according to the layouts in the cabinets.
Power supply system
The power supply system must provide equipment for a LAN system with a voltage of 220 V and a frequency of 50 Hz, with maximum allowable voltage fluctuations within ± 10% and frequency deviations of ± 0.4 Hz (according to GOST 13109-97).
All electrical wiring must be done in a three-wire circuit (phase, neutral, ground) with a wire that provides a ground connection for consumers, and all sockets must have a grounding contact.
All active devices in cabinets and switchgear enclosures must be grounded. The cross-section of the protective conductor is selected in accordance with the requirements of GOST R 50571.10-96, ПУЭ, СН 512- and technical documentation of the manufacturer for the hardware used.
The existing ground loop must meet the requirements of GOST R 50571.22-2000 and have a resistance of not more than 4 ohms.
The quality characteristics of the electric lighting system in the premises should be taken in accordance with SNiP 23-05-95 "Natural and artificial lighting" and ensure the comfortable work of the attendants during maintenance.
Ventilation and air conditioning system
The premises in which the LAN equipment will be located must be equipped with a system of general exchange supply and exhaust ventilation with air exchange in accordance with the requirements of SNiP 41-01-2003.
The ventilation and air conditioning system should ensure the continuous operation of the equipment and maintain the temperature and humidity conditions with the following parameters:
temperature - + (20-25) ° С;
relative humidity - (25-80)%;
the rate of temperature change is not more than 10 ° C per hour;
the rate of change of relative humidity of air - no more than 5% per hour.
Dust: allowed - not more than 0.75 mg / m³, with a particle size of not more than 3 microns.
